Do you know where your data is?
If that question makes you sweat, you’re not alone. The truth is there’s a pervasive gap between IT policy and practice across a plethora of organizations.
In the inaugural SANS Endpoint Data Survey, 169 security and IT professionals were asked where several types of their organization’s data exists and what they’re doing to keep it under lock and key.
While 62% of companies have policies prohibiting users from copying PII (personally identifiable information) onto endpoints (aka any device, including personally owned ones, through which a user accesses an organization’s networks, applications, or data), 80% of these orgs revealed their users were bringing said data onto their endpoints anyway.
Yep, 80% of organizations have sensitive data saved on employee devices (which is against policy) despite the best intentions of IT leaders at most organizations and trainings designed to protect this sensitive info.
So, how can companies strike the right balance and keep files secure, no matter how employees need to work? We teamed up with CrashPlan to highlight some key data and better understand what human error and the challenges of endpoint security look like—and how both can be solved simultaneously and automatically.
When high volumes of data exist on endpoints in business settings (like on a manager’s laptop or a junior exec’s email app), data may not be adequately protected. A majority of respondents to the SANS Endpoint Data Survey reported that sensitive data is stored on employee computers in the form of files:
On the flip side, enforcing company protocol or expecting users to remember to manually back up data can negatively impact employee productivity…or just be done improperly. According to the SANS Endpoint Data Survey, 30% of IT leaders say employees in their organizations break company backup policies every day. 54% of those IT leaders say policies make it harder for users to get their work done, and 66% say policies are too hard to enforce.
When companies don’t back up their users’ computers, they run the risk of data loss if something goes wrong with the computer (malware, hardware failure or loss, accidental or malicious deletion, etc.). This also creates operational, financial, legal, and reputational repercussions.
This problem is starting to feel like a game of Whac-A-Mole for businesses. 54.8% of SANS respondents say they have technical controls in place to prevent users from copying personally identifiable information to their computers, but 79.7% believe their users are doing it anyway. (Great.)
The stats are similar for intellectual property, financial data, and technical data. Only 6.5% of respondents believe their organizations’ endpoints are free of personally identifiable information.
If bad actors (aka hackers of all sorts) get ahold of certain datasets, damage and deletion are all-too-real possibilities—not to mention that it could jeopardize a company’s reputation.
According to the survey, the risk most commonly associated with data damage or deletion was “operational.” It’s interesting to note that operational risks ranked higher than financial, compliance, reputational, strategic, and even legal risks for all data types (except financial).
Operational risk and impact can take many forms, including system downtime; lost employee productivity; the personnel required for incident response; the time and resources spent locating, restoring, or recreating lost or damaged data; and the involvement of teams (legal, compliance, and HR, for starters) outside of security. It’s basically the worst kind of domino effect.
In instances like these, lost productivity is inevitable, and risks are company-wide. Take a look:
Greatest Risk if Data is Damaged
Greatest Risk if Data is Deleted
Concern about operational impact is all the more understandable when you realize that the potentially damaged or deleted data is the exact info needed to maintain and restore technical services.
Another recent report, authored by TAG Infosphere found that 71% of CISOs wouldn’t be surprised by an endpoint data breach. After reading the above, it’s hard not to agree.
There needs to be a focus on closing the endpoint security gap. Company policies don’t seem to cut it, and cloud collaboration tools weren’t built for this kind of job.
Data resiliency starts with a solution like CrashPlan—backup that’s tailored to this sort of problem.
CrashPlan delivers an automatic endpoint backup solution that requires no action from the user. That’s right, nada. When employees work on files, those files are encrypted and backed up to the cloud every 15 minutes, so lost or damaged data can be restored quickly and easily by users.
And if there’s a breach of sensitive data due to ransomware, these backups provide viz into exactly what was breached, even if bad actors encrypt the data and hold it ransom. The best part? All data can be restored.
In short, human compliance is removed from the equation, creating a simplified and streamlined system. This addresses endpoint vulnerabilities and effectively alleviates IT headaches.
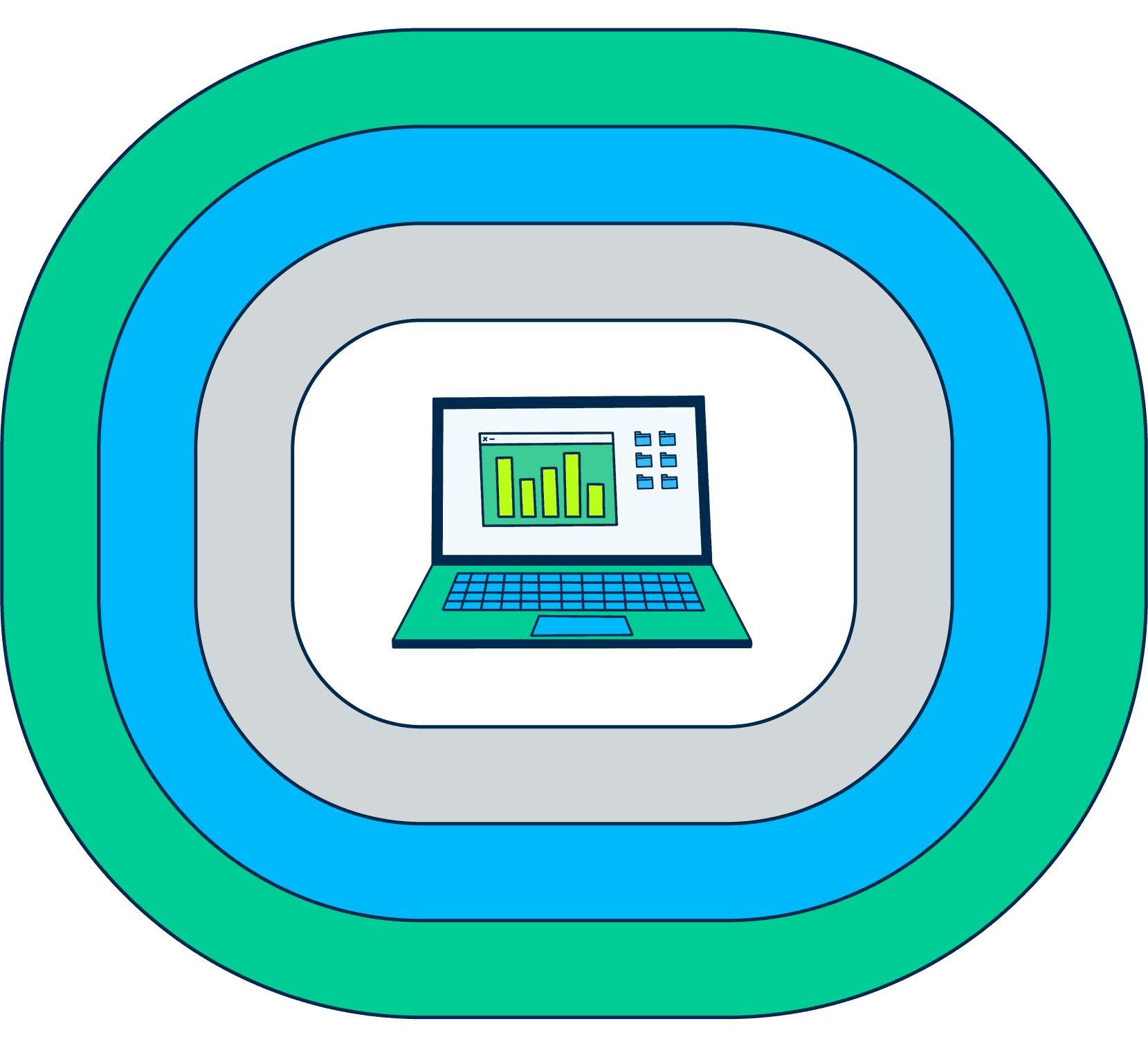
Want an example? TAG suggests its own model for a modern approach to endpoint security: MEAD (malware, EDR, analytics, and data). The MEAD framework puts an endpoint backup solution like CrashPlan at the center of the security stack, focusing on compact integration between CrashPlan and the organization’s other endpoint security tools (anti-malware, EDR, endpoint analytics products). Here’s what it looks like:
Pretty spiffy. Nothing quite like the sight of a protected and prepared system.